Welcome to the second half of our brief blog series on the dangers of fake apps and rogue security software. In Part 1, we took a look at fake apps. Among those discussed was the infamous Virus Shield, a fake mobile antivirus app that did not actually do anything. However, those who downloaded the fake app may want to consider themselves lucky that it didn’t. Had it been a rogue security software loaded with a virus (or worse), as we will show in this second installment, their situations could have been far more troublesome. In fact, a 2010 study by Google found that 15% of all malware is downloaded due to rogue or fake antivirus software.
As we’ve shown in multiple articles this year, cybercriminals—from hackers to data skimmers to identity thieves—have only become cleverer and more sophisticated in their methods over the years. However, their use of rogue security software actually isn’t all that new. In fact, reports of encounters with rogue security software date back to at least 2008 (possibly longer). While nothing new, these sorts programs have definitely become more frequent and harder to identify in recent years.
Rogue antivirus or rogue security software is more or less defined as a kind of Internet fraud in which cybercriminals exploit computer software vulnerabilities to deceive or mislead users into paying money for (or downloading for free) fake or malicious programs that they believe will remove malware, sometimes on order to employ some form of ransomware. Rogue security software may also claim to get rid of viruses or malware but, once downloaded, will instead introduce said viruses and malware to a computer.
Scary stuff, right?
The best case scenario is that if you downloaded one of these rogue programs, it simply doesn’t work as promised and you’re out the money you paid for it. Unfortunately, this scenario is pretty rare. Most of the time, these programs infect your computer with dangerous viruses, malware, or ransomware. This means that the poor users who are fooled into downloading such programs, while mistakenly believing they’re protecting their devices from viruses/malware, are actually voluntarily installing even more malicious software.
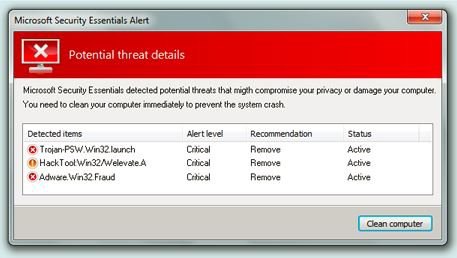
Here is an example of a common scenario that illustrates how most rogue antivirus software encounters play out:
It usually begins with a user just innocently browsing the internet, and most likely with Internet Explorer (sorry to the IE fans out there, but it is true). Everything seems to be fine until, suddenly, a very panicky-looking popup occurs that says something to the effect of “Warning! Your computer has been infected with a virus! Click here to protect your computer now!” These popups are designed to induce panic, in the hopes you’ll click without thinking (please… don’t do that).
At this point, the user likely responds with one of the following reactions, only one of which is correct:
Ill-Advised Reaction #1: The user fails to realize that the popup is a fake, or that it isn’t even from the same antivirus provider he or she uses, and clicks on the button. The result? Malware and/or a virus is downloaded, the user’s data is stolen, the screen is flooded with unending popups until the computer crashes, and/or (if its ransomware) the computer locks up.
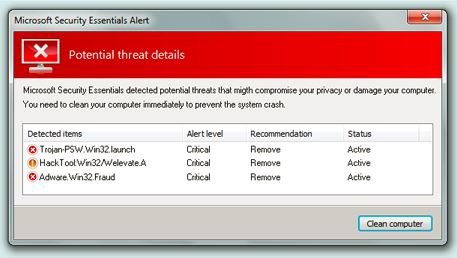 Ill-Advised Reaction #2: The user recognizes the popup as a fake. However, he/she decides to click on the “X” icon to close the popup window. The result? Malware and/or a virus is downloaded, the user’s data is stolen, the screen is flooded with unending popups until the computer crashes, and/or (if its ransomware) the computer locks up. That’s right, clicking the “X” icon to close a rogue window is just as dangerous as clicking the actual popup button. The cybercriminals who create these rogue popups do this on purpose, because they know people are more likely to react by clicking the “X” icon than a suspicious popup button.
Ill-Advised Reaction #2: The user recognizes the popup as a fake. However, he/she decides to click on the “X” icon to close the popup window. The result? Malware and/or a virus is downloaded, the user’s data is stolen, the screen is flooded with unending popups until the computer crashes, and/or (if its ransomware) the computer locks up. That’s right, clicking the “X” icon to close a rogue window is just as dangerous as clicking the actual popup button. The cybercriminals who create these rogue popups do this on purpose, because they know people are more likely to react by clicking the “X” icon than a suspicious popup button.
Proper Reaction: The user recognizes that the popup is a fake. The user is careful not to click anywhere on the popup, including the “X” icon, and instead shuts down the browser safely (Windows: ctrl + alt + delete; click “task manager”; select the browser; click “end process”). The user then shuts down the computer entirely and reboots. Hopefully, the user then installs a safer web browser (Internet Explorer is extremely vulnerable to rogue popups) such as Firefox, Chrome, or Safari. If the popup returns after the reboot, the user should repeat the shutdown process again. Instead of rebooting, however, the computer should remain powered down and be taken to a professional.
Rogue Security Software: Know the “Red Flags”
Here are some tell-tale red flags that can help you to identify the presence of rogue security software:
- The software comes with a rather high-pressure pitch, using phrases like “Your computer is AT RISK! Download our software RIGHT NOW to protect your computer from viruses!” Reputable AV software firms don’t use such tactics.
- If downloaded, it generates a strangely high number of infection alerts
- You begin experiencing an unusually high number of popups when online, or you start getting popups when not online
- Your computer slows down significantly, especially while online (but even when you’re not)
Avoiding Rogue Security Software
Here are some helpful tips to keep you from being victimized by rogue security software:
- Ensure your computer has been installed with a legitimate and well-vetted antivirus software (here are links to AVs for both Windows and Mac users) with a strong firewall
- Remember to never open an email attachment unless you can verify the source
- Use any browser other than Internet Explorer
- Make sure your computer’s security settings are at an appropriately high level
- Be observant. Rogue AV often tries to mimic real programs, but there are usually subtle differences that are noticeable if you look closely (such as misspellings or pixelated logos)
- NEVER download freeware or shareware, unless you are 100 percent certain that it comes from a reputable source. Freeware and shareware programs, more often than not, actually come bundled with all sorts of spyware, adware, and/or fake antivirus programs
- Familiarize yourself with some of the more common rogue antivirus programs
- NEVER click on a popup advertising antivirus or security software. Legit AV software companies do not use popups
- If a virus alert appears on your screen, DO NOT click on it. As a matter of fact, you might just want to not touch your mouse at all. Instead, hit control + alt + delete and delete any rogue programs from the list of running programs. If this doesn’t work, contact your computer manufacturer’s tech support or take it to a professional
Too Late (You Just HAD to Click on It… Didn’t You?)
Let’s say it’s too late. You clicked on the window, and now your computer is infected. To be honest, the best thing you can do at this point (well… the only thing, really) is shut down your computer until you can take it to a professional and get your hard-drive sanitized. The worst thing you can do is keep on using an infected computer.
Remember, these things are called “viruses” for a reason.
The longer you use an infected computer, the farther they spread and the more damage they cause. Honestly, continuing to use a virus-infected computer is a really good way to transform it into a rather expensive paperweight… not to mention that, if you’ve downloaded spyware, you’re just giving cybercriminals even more opportunities to steal your information.
Keep Calm and Stay Cyber Safe
As more people become aware of (and terrified by) scary things like viruses, adware, malware, spyware, and ransomware, the more cybercriminals are trying to profit from their panic with rogue antivirus. Stay calm. Trust your instincts. Be alert. These, along with the information in this article, are all the tools you need to avoid becoming yet another victim of hackers and identity thieves.
Keep calm and stay cyber-safe, dear readers.
HERE ARE SOME RELATED ARTICLES YOU MAY FIND INTERESTING
Ophthalmology | Plastic Surgery | Security | cybersecurity | ransomware | Dermatology | Online Reputation | Regulatory & Compliance | Orthopedics | Security & Data Management | HIPAA
Ransomware Attacks Happen Every Day, Is Your Practice Safe?
By: Nextech | September 29th, 2022
Security | Regulatory & Compliance | Security & Data Management
Performing Your Annual Security Risk Assessment
By: Heather Miller | June 22nd, 2021
Security | Security & Data Management
Avoiding a security scandal in your practice [VIDEO]
By: Nextech | May 12th, 2015