Latest Articles
The latest news and information regarding electronic medical records, practice management software, HIPAA, and security from Nextech.

Patient Engagement | Healthcare Technology
By:
Nextech
March 20th, 2015
Even with vast improvements in patient engagement and scheduling methods, no-showscontinue to be a major concern for practices. When a patient fails to arrive for his or her appointment, it has a negative impact on clinical workflow in a variety of ways, especially when it comes to financial losses. What do no-shows cost providers? A North Carolina-based study looked into the costs of no-shows for health care providers. The researchers created a situational model that applied the average non-attendance rate of 18 percent to a schedule of 24 patients in one day. With perfect attendance, the net gain would have been $4,433.32, but a no-show rate of 18 percent would mean a loss of $725.42, reducing the net gain to $3707.90.

By:
Nextech
March 18th, 2015
Hello, and welcome to the Nextech blog! Today we'll be discussing why specialty physicians require specialty EHRs.
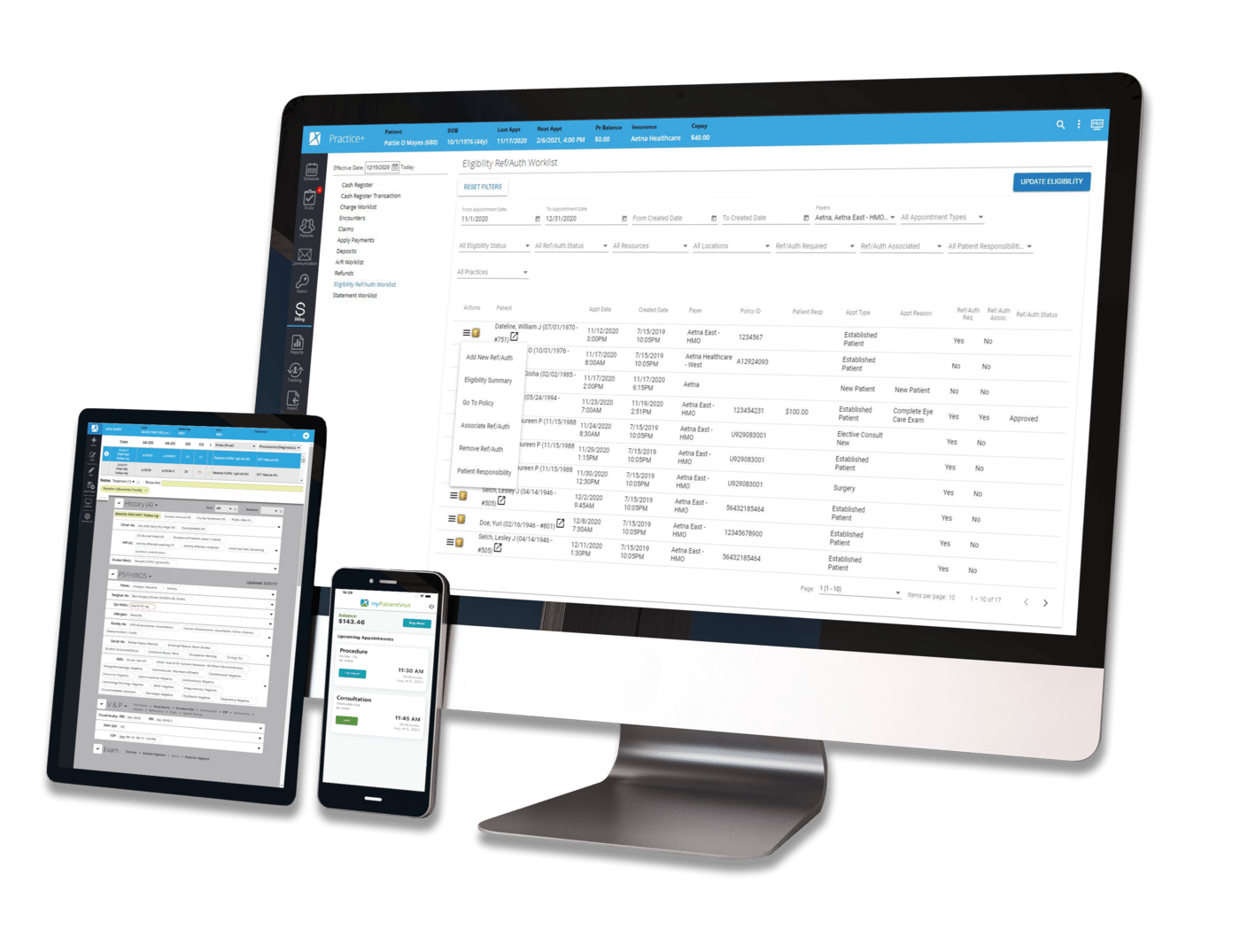

Regulatory & Compliance | Security & Data Management | Healthcare Technology
By:
Nextech
March 17th, 2015
Welcome to the final installment of this blog series—creating a healthcare BYOD policy. You need one of these for a number of reasons. First and foremost, it’s a HIPAA/PHI issue. All the security tools in the world are powerless in the face of human error, and mistakes happen. If and when you have a lost/stolen device, one of the first things HHS is probably going to ask for is a copy of your office’s BYOD policy. Trust me, “What policy?” is not an acceptable answer.

Security & Data Management | Healthcare Technology
By:
Nextech
March 16th, 2015
Anyone in the healthcare industry who plans on adopting a BYOD environment needs to be aware that HIPAA standards strongly recommend (though they do not require) “encryption of all corporate email, data, and documents, in transit and at rest, on all devices” that contain Protected Health Information (PHI). The law does not specifically state that they require you to have encryption. Instead, it just says that healthcare providers with BYOD are “asked” to have it. However, what do you think would happen when and if a PHI breach occurred because your office had a lost/stolen device that wasn’t encrypted? Do you think HHS would show mercy and just decide to let it pass this time?

Security | Regulatory & Compliance | Security & Data Management | Healthcare Technology
By:
Nextech
March 13th, 2015
Now that you’ve had some time to weigh the pros and cons of adopting BYOD, it is time to start working up an adoption plan. For any workplace, this requires researching and investing in certain mobile security tools. It also means addressing a number of key infrastructure and staff issues. Those in the healthcare industry must consider issues such as maintaining devices and network security, just as any other workplace would. However, those in healthcare have additional components they must take into consideration when it comes to BYOD—HIPAA compliance and securing Protected Health Information (PHI). As already mentioned in Part 1, HIPAA violations and PHI breaches can be extremely costly.

Security & Data Management | Healthcare Technology
By:
Nextech
March 12th, 2015
What is BYOD? For those who may not already be familiar with it, BYOD stands for “Bring Your Own Device,” and it refers to the practice of allowing employees to bring and utilize their own computing/mobile devices—smartphones, tablets, laptops, etc.—within the office/company to be used for business/work purposes, including allowing them to connect to a company’s secure network with said devices. A plethora of blogs and news articles on the topic of BYOD have been popping up all over the internet in recent years. While some articles express various apprehensions and concerns about BYOD, often claiming it presents an unsolvable security risk situation, a great many more of these articles point to BYOD as the “new normal,” a necessity of conducting business in the New Media Age. Whether for or against the practice of BYOD, however, it seems as if everyone is going to have to accept it at this point, because it looks like it’s here to stay.

By:
Nextech
February 27th, 2015
The rise of technological accessibility has had a pronounced effect on every single genre of the professional world across the last few years. Perhaps no single industry, though, has seen an explosion of innovation equal to that which has occurred in the medical field. Whether you're a doctor, a practice manager or simply interested in the growth of the medical field, you've no doubt noticed the rise of electronic medical records. Simpler and more efficient than alternative methods, EMRs have become a mainstay of most successful practices in the U.S.

By:
Nextech
February 25th, 2015
Hi, and welcome back to the Nextech blog! Today we're going to be discussing using mobility solutions to move your electronic health records system beyond the desk and PC.