Latest Articles
The latest news and information regarding electronic medical records, practice management software, HIPAA, and security from Nextech.

cybersecurity | Security & Data Management
By:
David Slazyk
January 24th, 2025
As the Chief Information Officer at Nextech, I’ve seen how cybersecurity threats have grown in scope and sophistication. Healthcare practices are facing a major increase in attacks, from ransomware to zero-day vulnerabilities posing risk to patient data and the continuity of care.

Plastic Surgery | EHR | data | ASC | Revenue Cycle Management | Security & Data Management | Advanced Analytics
By:
Tom Robinette
May 26th, 2023
The proliferation of ambulatory surgery centers (ASCs) among private medical practices — including plastic surgery specialists — has been steadily rising for years. The volume of outpatient surgeries performed in ASCs grew 32% over a 12-year span, according to a Bain & Company report. The Covid-19 pandemic has accelerated the expansion of ASCs even further, and there are now estimated to be more than 11,000 ASCs across the U.S.
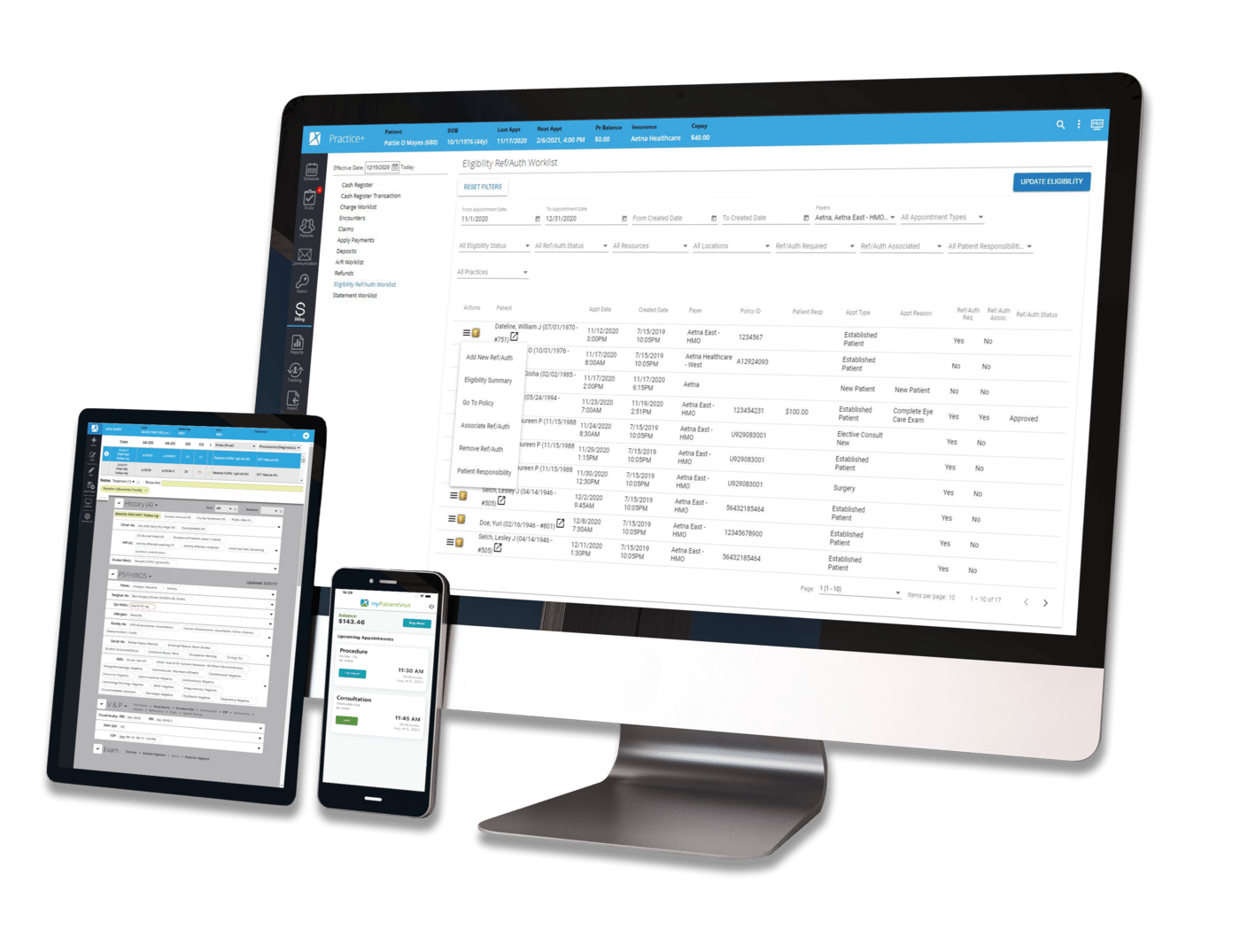

Ophthalmology | Meaningful Use | EHR | Interoperability | MIPS | Regulatory & Compliance | Security & Data Management | Clinical Efficiency | IRIS Registry
By:
Nextech
July 26th, 2022
For almost a decade, Nextech EHR has integrated with the IRIS® Registry. But what is the IRIS Registry and why does it matter?

By:
Nextech
December 16th, 2021
On December 9th, 2021, a critical vulnerability was discovered in a popular code library, Log4J, that affected many applications across the world. It affected everything from firewalls to security software. Essentially, anything that uses this library and takes user input is potentially vulnerable. Researchers have named this vulnerability Log4Shell.

Patient Engagement | Security & Data Management | Healthcare Technology | Front & Back Office Performance
By:
Nextech
November 23rd, 2021
Do you know what time it is? It’s turkey time, people! (Apologies to the vegetarians out there). But yes, Thanksgiving is upon us once again. As per tradition, this is the time of year when we consider the things for which we are most thankful (and spend a whole day eating ourselves into food comas and then the brave or mad among us choose to go out the next day for an annual shopping event with its own casualty rate). And this Thanksgiving there are certainly a lot of things to be thankful for—we aren’t locked up in our houses like we were last year, COVID vaccines are widely available, new episodes of Dexter are back on Showtime, and it looks like we will be able to openly travel this holiday season (and on that note, if you do travel, please be kind to airline personnel).

Security & Data Management | Healthcare Technology
By:
Nextech
October 26th, 2021
Welcome back to the blog, ghouls and goblins! It’s almost Halloween once again, that time of year when we celebrate all things scary. Perhaps one of the scariest things going on right now is the fact that many specialty practices still believe that having an onsite server infrastructure is somehow faster and more secure than using cloud-based solutions. It’s not. In fact, it’s terrifying to think about how on-premise systems are still out there giving nightmares to specialty practices like a burn-scarred maniac with a bladed glove.

By:
Nextech
October 12th, 2021
Well, folks… it’s that scary time of year once again. No, not Halloween. It may be October, but in this blog, we won’t be talking about ghouls and goblins. Nope. As you may already know, October is also Cybersecurity Awareness Month. And there are scarier things out there to worry about than those imaginary monsters in your closet.

Security | Regulatory & Compliance | Security & Data Management
By:
Nextech
June 22nd, 2021
Performing a regular security risk analysis (SRA) helps your practice stay HIPAA-compliant and protect patient data. A MIPS SRA also boosts your Merit-based Incentive Payment System score, leading to a higher chance of receiving a Medicare reimbursement at the end of the year.