Latest Articles
The latest news and information regarding electronic medical records, practice management software, HIPAA, and security from Nextech.

Best Practices | Patient Payments | Security | Financial Management
By:
Hannah Celian
July 2nd, 2024
Embezzlement within healthcare practices may be more prevalent than you realize, and the consequences of ignoring appropriate security measures can be severe. Medical Group Management Association surveyed nearly 1,000 medical practices and 83% reported being victims of embezzlement at some point in their operation. International Business Machines Corporation also reported in 2021 that healthcare breaches cost $9.23 million per incident — a $2 million increase over the previous year.
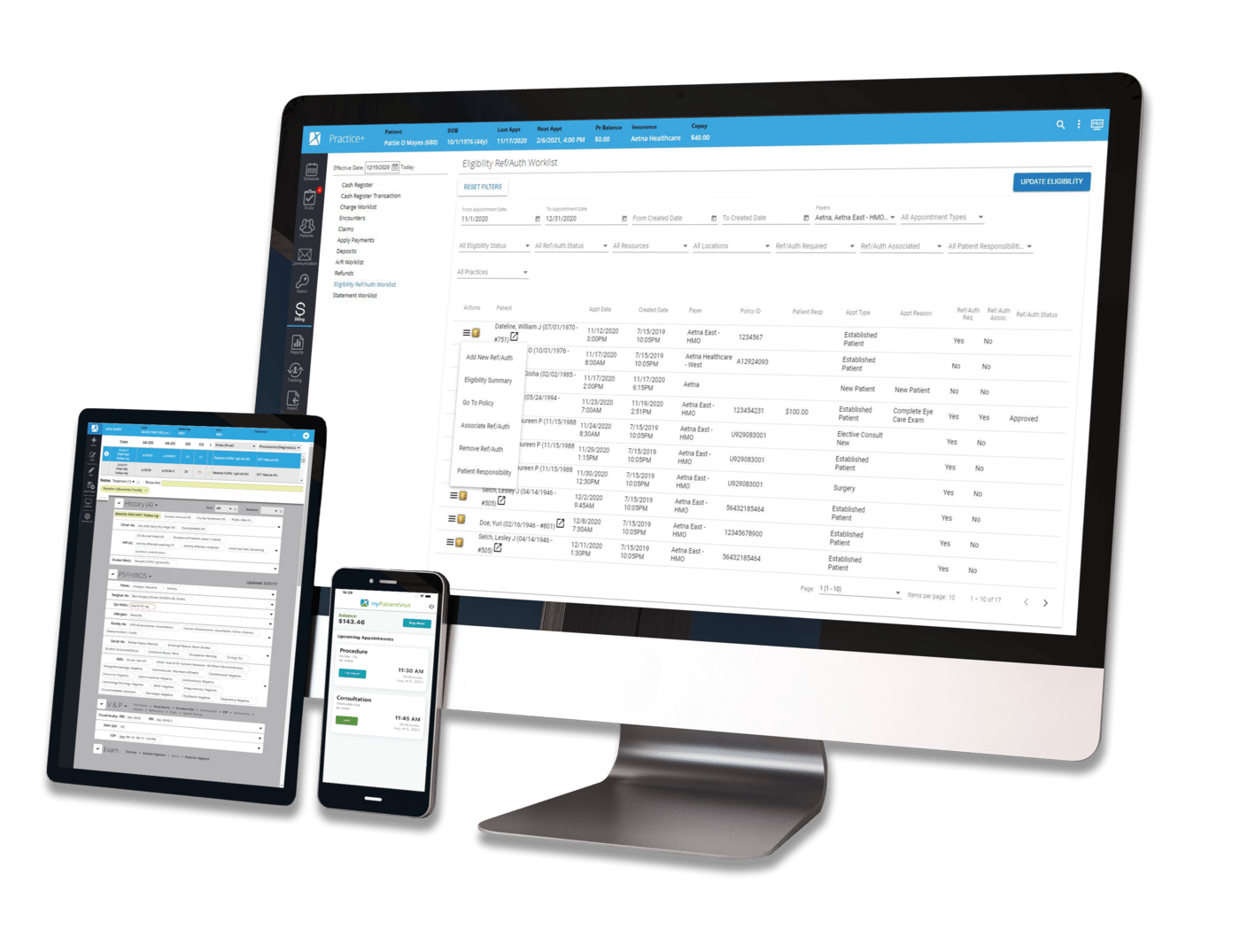

Security | Regulatory & Compliance | Security & Data Management
By:
Nextech
June 22nd, 2021
Performing a regular security risk analysis (SRA) helps your practice stay HIPAA-compliant and protect patient data. A MIPS SRA also boosts your Merit-based Incentive Payment System score, leading to a higher chance of receiving a Medicare reimbursement at the end of the year.

Security | Security & Data Management
By:
Nextech
June 30th, 2015
Welcome to the second half of our brief blog series on the dangers of fake apps and rogue security software. In Part 1, we took a look at fake apps. Among those discussed was the infamous Virus Shield, a fake mobile antivirus app that did not actually do anything. However, those who downloaded the fake app may want to consider themselves lucky that it didn’t. Had it been a rogue security software loaded with a virus (or worse), as we will show in this second installment, their situations could have been far more troublesome. In fact, a 2010 study by Google found that 15% of all malware is downloaded due to rogue or fake antivirus software.

Security | Security & Data Management
By:
Nextech
May 12th, 2015
Security breaches are likely to be at the forefront of your concerns when it comes to managing your practice. Still, you may not be doing everything in your power to avoid them. Take a look at these helpful tips for managing your practice's security.

Security | Regulatory & Compliance | Security & Data Management | Healthcare Technology
By:
Nextech
March 13th, 2015
Now that you’ve had some time to weigh the pros and cons of adopting BYOD, it is time to start working up an adoption plan. For any workplace, this requires researching and investing in certain mobile security tools. It also means addressing a number of key infrastructure and staff issues. Those in the healthcare industry must consider issues such as maintaining devices and network security, just as any other workplace would. However, those in healthcare have additional components they must take into consideration when it comes to BYOD—HIPAA compliance and securing Protected Health Information (PHI). As already mentioned in Part 1, HIPAA violations and PHI breaches can be extremely costly.

Security | Security & Data Management
By:
Nextech
February 5th, 2015
The last two decades have seen an unprecedented rise in technology both at home and in the workplace. This transition has affected all aspects of our lives, both public and private, and physicians practices are no exception to this statement. While advances in technology have largely been positive for the world of medicine, it's impossible to ignore the fact that a host of new security concerns have come along with this rise in user-friendly systems. When determining which EMR software best suits the needs of your practice, it's important to consider the specific situations and security concerns that your clinic or office will undergo on a daily basis. With that in mind, take a look at some of the most common security concerns affecting doctors' offices today: