Latest Articles
The latest news and information regarding electronic medical records, practice management software, HIPAA, and security from Nextech.

Regulatory & Compliance | Security & Data Management
By:
Nextech
June 5th, 2017
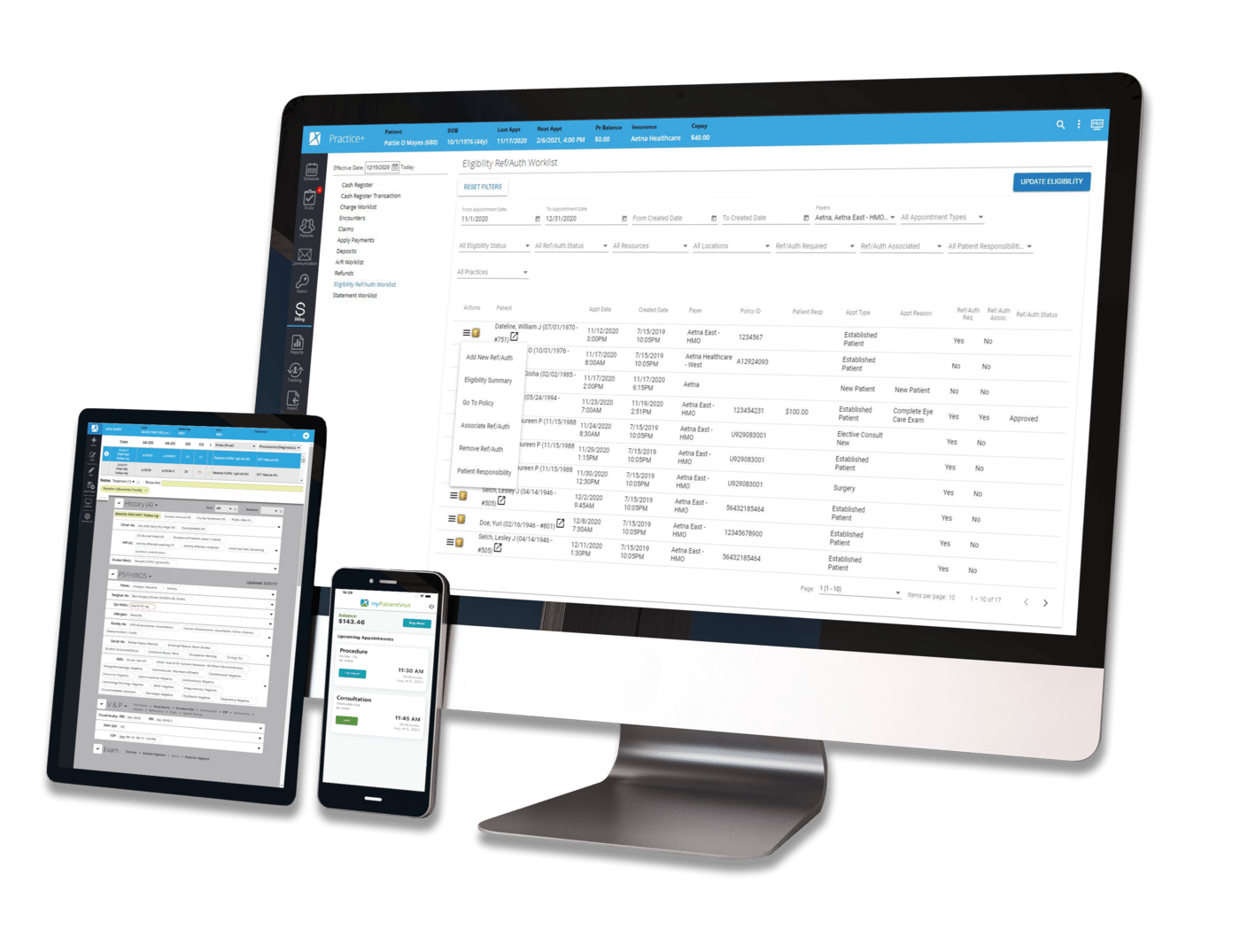
Your electronic medical record (EMR) and practice management (PM) systems capture a lot of information with every patient encounter. Having technology capable of creating reports and presenting them in a useful way allows you to quickly make key business decisions to improve or maintain peak practice performance in areas from clinical efficiency to financial measures. However, practices that do not take advantage of such solutions may miss out on opportunities or be delayed in making important decisions.

By:
Nextech
June 3rd, 2016
Not even the NFL is safe from the recent rise in stolen healthcare data. According to a report from Deadspin, a laptop belonging to an athletic trainer for the Washington Redskins was stolen out of the trainer's car after it was broken into. The laptop was located in a backpack, which was taken during the robbery.

Security & Data Management | Healthcare Technology
By:
Nextech
May 31st, 2016
Visit any healtchare IT blog today and it's likely you'll see a barrage of articles pertaining to cybersecurity - and for good reason. The healthcare industry has been especially vulnerable to cybersecurity attacks through tactics such as ransomware or data hacking, which is why the College of Healthcare Information Executives (CHIME) decided to do something about. In a press release on Tuesday,CHIME announced the creation of the Cybersecurity Center and Program Office.

Regulatory & Compliance | Security & Data Management | Healthcare Technology
By:
Nextech
May 26th, 2016
Every day, it seems something new is happening in the healthcare industry. Whether it's greater innovations in technology, breaking compliance news or even the growing threat of data hacking, there's a lot going on in healthcare. So you're able to catch up on all of the relevant news, lunchtime links will be a valuable resource for you to read about what's going on in the industry in one place, rather than searching all over the Internet.

Regulatory & Compliance | Security & Data Management
By:
Nextech
May 10th, 2016
"This matters. It's a matter of life and death." Those were the words of Vice President Joe Biden on Monday when he spoke at the Health Datapalooza in Washington, DC. The importance of healthcare IT and data sharing isn't lost on Biden. He experienced it firsthand as his son, Beau, was fighting cancer over a year ago. The Vice President described how difficult it was for the different hospitals his son received care at to share information.

By:
Nextech
April 15th, 2016
Data breaches are becoming an all too common occurrence in today's society. That could be quite an understatement for the healthcare industry, according to one report. An Internet Security Threat Report conducted by Symantec found that 39 percent of all data breaches in 2015 were within the healthcare industry.

By:
Nextech
April 11th, 2016
Ransomware is becoming more common and the healthcare industry has recently been a favorite target of hackers. With five ransomware attacks on healthcare organizations in the last month, healthcare organizations need to pay more attention to combatting ransomware.

By:
Nextech
April 8th, 2016
This has been a crazy month for ransomware attacks and, unfortunately, the vast majority of them have been focused on healthcare facilities and providers. In fact, no less than five healthcare organizations have been hit in just the last 30 days (and those are just the ones we know about because they were actually reported). On March 30, King’s Daughters Health in Madison, Ind. had to shut down their EMR after finding a user file infected with a well-known form of ransomware dubbed “Locky.” Then, on April 4, operations at MedStar Health were brought to a screeching halt by a ransomware attack that locked their EMR and demanded a payment of roughly $19,000 worth of Bitcoin to release the data. MedStar chose not to pay the ransom, instead taking the time to restore their system via backups. However, I would bet dollars to donuts that doing so ended up costing them far more than $19,000 when all was said and done.