Latest Articles
The latest news and information regarding electronic medical records, practice management software, HIPAA, and security from Nextech.

By:
Nextech
April 10th, 2015
Don’t Panic! (About Meaningful Use Stage 3) Part 2: The 2015 Certification Requirements in a Nutshell “The certification criteria we have proposed in the 2015 Edition will help achieve that vision through provisions that consider the range of health IT users and uses across the care continuum, including those focused on interoperable standards, data portability, improved transparency, privacy and security capabilities, and increased oversight." —Karen DeSalvo, MD. ONC Welcome to the second half of our series on Meaningful Use Stage 3. In Part 1, we looked at the interoperability and EHR function requirements of the CMS rule. In this article, we will look at criteria from the ONC 2015 rule. To be honest, I suspect the ONC’s 700+ page rule may have been responsible for a lot of the panic attacks folks seemed to have in response to MU3. Whereas the CMS rules are relatively straightforward, easy to follow, and seem to have the intent of stabilizing things, the ONC rule seems to be trying to do the opposite. Seriously, it’s almost like they’re trying to sow chaos. But remember: Don’t Panic… We can (and will) survive this.

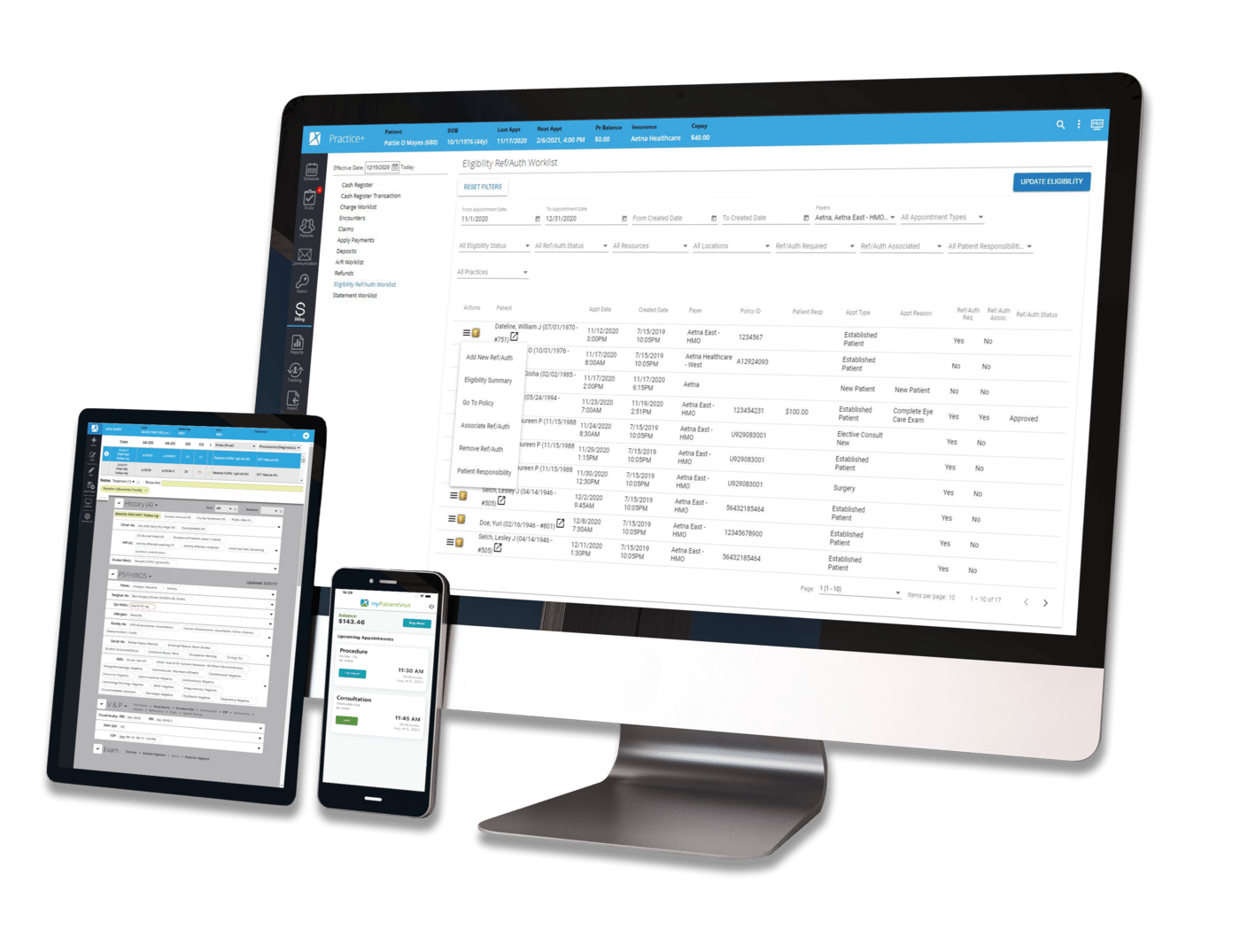
Patient Engagement | Healthcare Technology
By:
Nextech
April 9th, 2015
Transcript Hello, and welcome to the Nextech blog! Today we will be speaking about how to improve and increase use of your patient portal. First and foremost, Medical Practice Insider reports that you'll need to make sure that your patients are aware of the patient portal and how to use it. While they may not know the ins and outs of electronic medical records, you should take some time out of their next visit to introduce them to the concept and field any initial questions. Physicians could spend a couple of extra minutes with patients to educate them on benefits of a patient portal and answer their questions. It might also be helpful to have a portal kiosk on site where they can set up their account while they wait.

Regulatory & Compliance | Security & Data Management
By:
Nextech
April 7th, 2015
The protection and security of electronic medical records is a topic of growing concern. While the public may be focusing on the issue of breaches due to recent data hacks, the Office of Inspector General is turning its attention to EHR fraud. The OIG is calling for the Centers for Medicare & Medicaid Services to address the issue of EHR fraud vulnerabilities. In a March 2015 report, the OIG claimed that the agency has not adequately implemented fraud safeguards. "HHS must do more to ensure that all hospitals' EHRs contain safeguards and that hospitals use them to protect against electronically enabled healthcare fraud," OIG officials wrote in the report.

By:
Nextech
April 6th, 2015
Part 1: Interoperability & EHR Function Measures On March 20 2015, The Centers for Medicare & Medicaid Services (CMS) released Stage 3 of their Electronic Health Record Incentive Program. At the same time, the Office of the National Coordinator for Health Information Technology (ONC) released the 2015 Editions of the Health Information Technology Certification Criteria, Base Electronic Health Record Definition, and ONC Health IT Certification Program. This news has resulted in some rather extreme reactions among some in the healthcare industry—for example, absolute panic and unbridled rage. This seems rather odd. Come on… it’s not like we weren’t aware that this was coming. As a matter of fact, I’m pretty sure that I gave everyone a heads up about this back in January. Based on how certain people are behaving, though, you’d think the CMS & ONC just surprised all of us with this stuff like it’s some kind of weird fire drill. Then again, trying to make sense out of so much complicated (and, let’s face it, very boring) text is probably enough to make anyone a little irritable.

By:
Nextech
March 31st, 2015
Just about any business, especially in healthcare, is likely already covered by some kind of general liability insurance. Such policies are standard, providing coverage for events such as bodily injury and/or property damage that result from the insured’s operation, product, and/or building/site. However, these types of policies were created long before the days of cybercrime. They were never meant to cover liability or loss from things like cyberattacks and data breaches. Therefore, these policies rarely if ever cover losses due to cybercrime. In fact, just about all general liability policies now come with very specific language about the fact that they do NOT cover such losses or costs due to cyber-incidents. This means many businesses have no choice but to turn to cyber insurance… and so they should.

By:
Nextech
March 30th, 2015
Some readers might remember the Anthem data breach, in which around 78.4 million people had their records compromised, that I briefly mentioned at the start of our cybersecurity blog series. At the time, the cause of that breach had not yet been made public. By a funny (or, perhaps not so funny) coincidence, it turned out to be the result of spear-phishing (which that article covered) and was further compounded by factors such as Anthem’s lack of data encryption and their poor password security practices. One would think that the catastrophic and very public data breach at Anthem would have served as a strong warning to other such organizations, and that they would have taken steps to prevent the same from happening to them.

Regulatory & Compliance | Financial Management
By:
Nextech
March 26th, 2015
Even with the most effective medical billing software, all medical practices experience some level of claim denials (when insurance companies refuse to honor requests for health care coverage). According to the American Academy of Family Physicians, the average denial rate for providers is between 5 and 10 percent. However, the general goal is to keep that number below 5 percent, as a lower denial rate means a more abundant cash flow.