Latest Articles
The latest news and information regarding electronic medical records, practice management software, HIPAA, and security from Nextech.

By:
Nextech
March 11th, 2015
In a February series of Nextech webinars, James H. Leach – CEO of Detroit-based E&M Consulting, a national supplier of training in medical documentation and coding, shared his perspective on ICD-10. Presenting separately to providers in ophthalmology, dermatology and plastic surgery, Leach began each webinar with a helpful pointer on reference materials and good advice about “diving in.” In his opening comments:

By:
Nextech
March 10th, 2015
Hello, and welcome to the Nextech blog! Today we will be discussing key differences between ICD-9 and ICD-10. As you probably already know, the largest single difference between these two coding languages is that ICD-10 is far more expansive than the over 30 year old ICD-9 code set. ICD-9, with a total of 14,000 diagnosis codes and 4,000 procedure codes, is somewhat limited in its ability to describe and denote patient conditions and procedures. ICD-10 will be able to generate 68,000 diagnosis codes and 87,000 procedure codes. This added range of capability is due to an expansion of the coding structure. The transition, scheduled for October 1, 2015, is still a daunting undertaking for those who did not move to electronic medical records for Meaningful Use. Nextech has a unique approach to simplifying ICD-10 by building codes for you while you chart. Thanks for watching the Nextech blog, and be sure to check out our other ICD-10 resources.
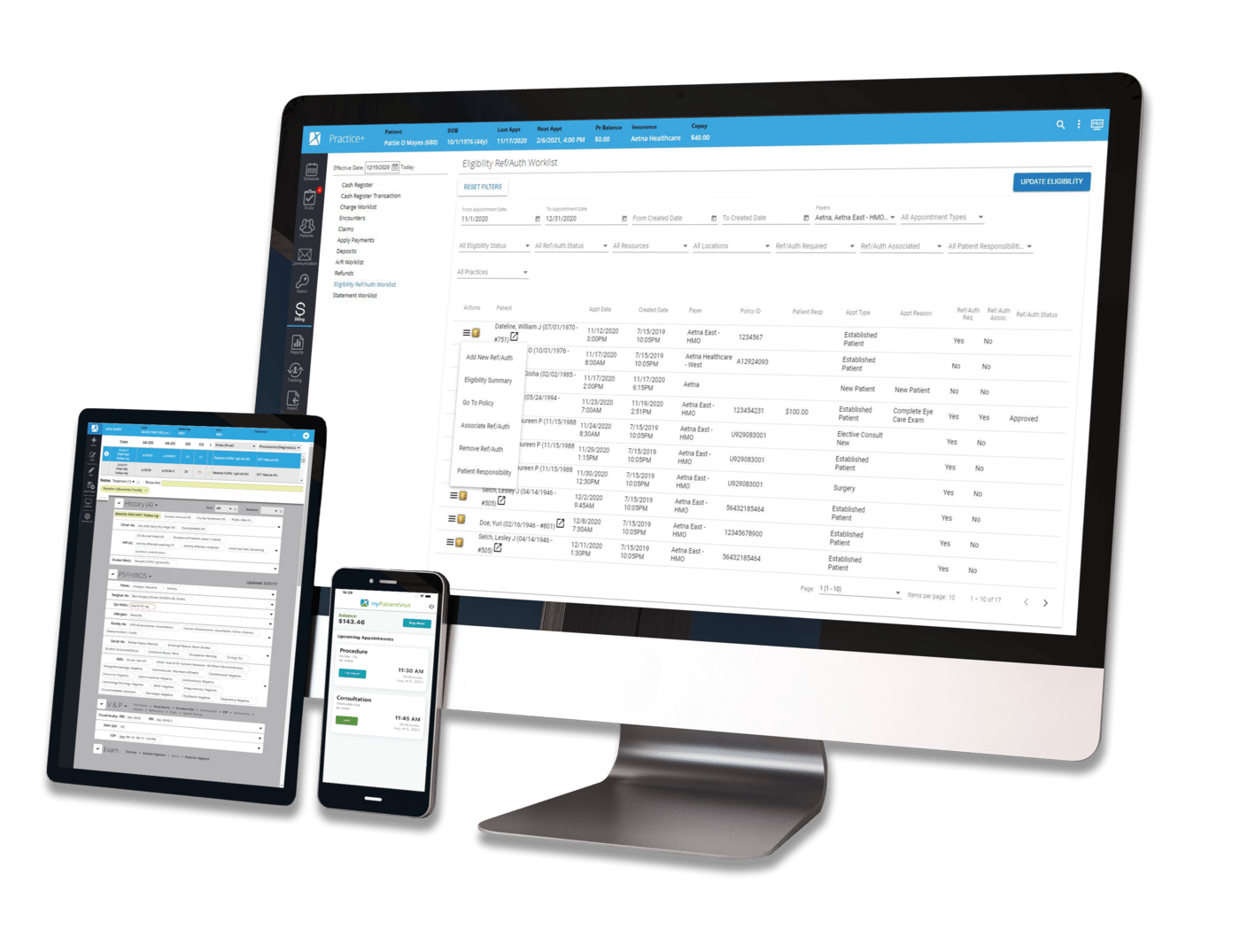

By:
Nextech
March 9th, 2015
Yelp is a popular application for crowd-sourced reviews of restaurants, retail stores and a wide array of other local businesses; however, it is also growing in prominence among healthcare providers. It utilizes a word-of-mouth approach to allow patients to give their opinions concerning patient engagement, quality of care and any other aspect of the practice, and it serves as an essential application for patients searching for everything from general practitioners to dermatology specialists.

By:
Nextech
March 6th, 2015
Any individual who has spent a number of years as a medical professional will tell you that no two doctor-patient relationships are going to be exactly the same. Working in health care, you have the opportunity to interact with individuals from all backgrounds. So in order to provide the appropriate type of care, you'll need a varied and flexible skill set as a provider. Among the largest determining factors in how you interact with a patient is his or her age. Young patients or children will require a different sort of approach than adults, as will senior citizens. If your practice treats a wide range of patients, than it is particularly important to understand generational differences.

By:
Nextech
March 3rd, 2015
As technology continues to grow and evolve before our eyes, social media has permeated nearly every aspect of our daily lives. We look to it for information regarding the news, cultural events, our friends and everything in between. That said, it's no surprise that medical practices that may have never considered blogging several years ago are sprouting up on social media. If your practice is just starting out in this realm, though, it can be difficult to know where to begin. Take a look at these tips to ensure you're setting off in the right direction:

By:
Nextech
March 2nd, 2015
We’ve posted a number of discussions on this blog, in recent months, addressing various issues related to the upcoming transition from ICD-9 to ICD-10. By now, everyone in the healthcare industry should at least be aware that October 1st 2015 is the final deadline for ICD-10 implementation in the United States. A further delay to this deadline failed to pass when Congress approved their “Omnibus” federal funding bill at the close of 2014. Some of those who were still holding out (hoping a delay would allow them another year or two of ICD-9) are now scrambling to be ICD-10 compliant before the deadline, to prevent having their insurance claims denied due to improper coding.

By:
Nextech
February 27th, 2015
The rise of technological accessibility has had a pronounced effect on every single genre of the professional world across the last few years. Perhaps no single industry, though, has seen an explosion of innovation equal to that which has occurred in the medical field. Whether you're a doctor, a practice manager or simply interested in the growth of the medical field, you've no doubt noticed the rise of electronic medical records. Simpler and more efficient than alternative methods, EMRs have become a mainstay of most successful practices in the U.S.

By:
Nextech
February 26th, 2015
Between keeping up with advances in modern medicine, establishing meaningful and healthy relationships with your patients and dealing with the day-to-day grind of running a business, it can be hard to make time to think critically about revenue cycle management. Still, it's important to remember that having a clear understanding of your various revenue streams and financial management techniques is key to the longevity and success of your practice. Luckily, this need not be quite as difficult an undertaking as it may first seem. In fact, pairing strong organizational techniques with effective practice management software can make financial evaluation a breeze. Take a look at these best practices for managing the financial health of your practice: