Nextech Blog
The latest news and information regarding electronic medical records, practice management software, HIPAA, and security from Nextech.

Technology & Innovation | Aesthetics | AI
By:
Tyler Terry
May 6th, 2025
In the world of aesthetic treatments, it’s natural to feel a mix of excitement and hesitation. Technologies like AI simulators promise to ease nerves by predicting how you might look after a treatment. It’s an appealing idea — a digital crystal ball tailored to your face.

By:
Heather Miller
May 2nd, 2025
If your practice accepts Medicare, participating in a Medicare Quality Payment Program (QPP) is an essential part of maximizing your reimbursements.

MedSpa | Aesthetics | podcast
By:
Hannah Celian
May 1st, 2025
Most aesthetic practices aren’t prioritizing before-and-after photos the way they should. Candace Crowe drives home the importance of photography in patient decision-making and shares the best practices for capturing meaningful results while making patients feel comfortable throughout the process.

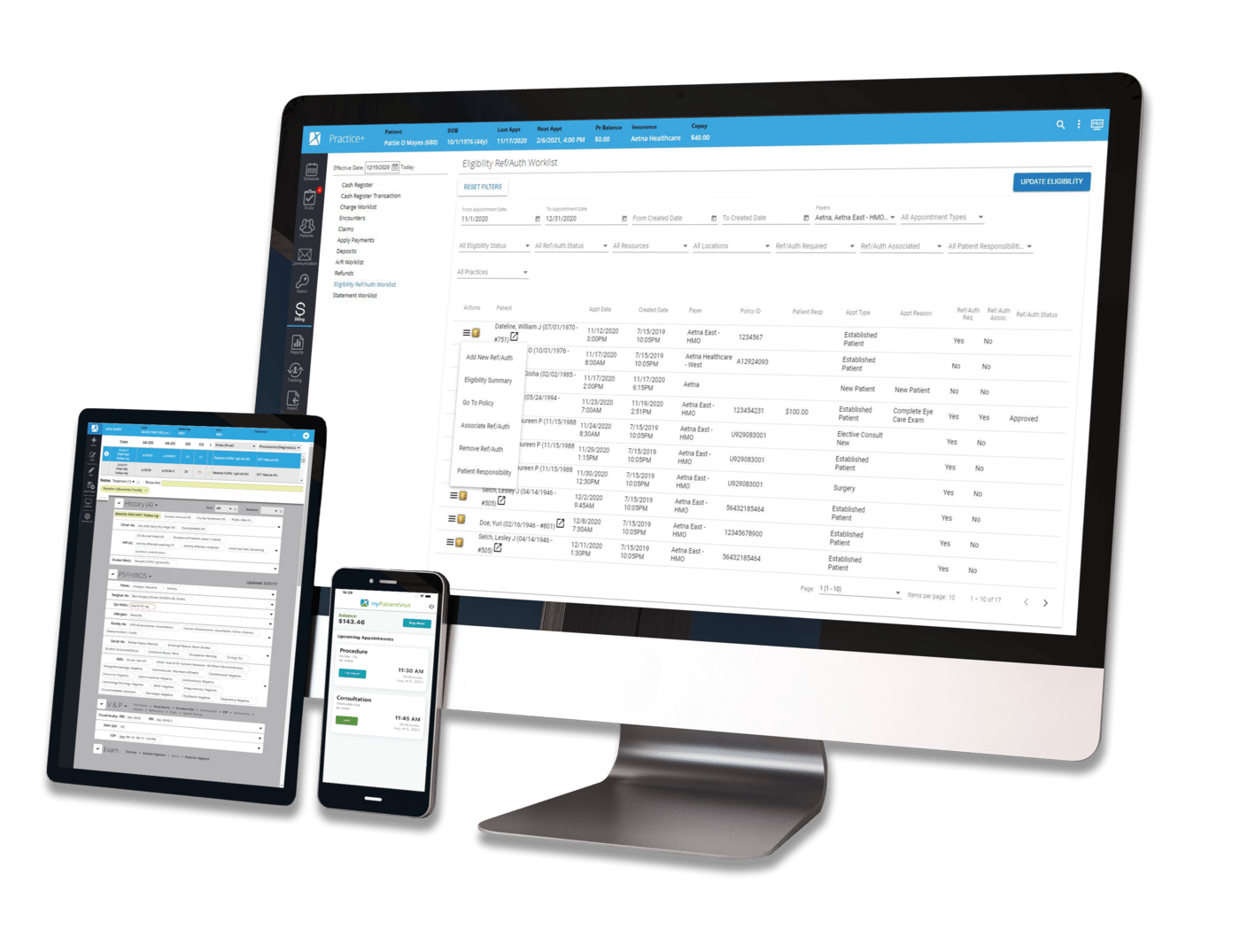
Billing | Revenue Cycle Management
By:
Nextech
April 29th, 2025
The CMS 1500 form is a critical part of the revenue cycle for private practices. It’s a standardized way to get reimbursements from Medicare, Medicaid, and many private insurance carriers. Standardized, however, isn't synonymous with easy-to-navigate. Ahead, we’ll dive into the components of the CMS 1500 form, when your practice should use it, and strategies to simplify and speed up your payment reconciliation process.

Patient Engagement | Patient Care
By:
Nextech
April 28th, 2025
Creating a seamless patient check-in process at your clinic is a balancing act. On one hand, your practice wants to provide an excellent first impression to patients. However, your staff have limited bandwidth, which can diminish their ability to administer a comprehensive patient check-in process as they must also juggle other important responsibilities.

MedSpa | Aesthetics | podcast
By:
Hannah Celian
April 23rd, 2025
What really sets top med spas apart? Kirstie Jackson, Director of Education at AmSpa, has spent over 20 years in the aesthetics industry, starting in the UK before making her mark in the US, and she’s here to break it all down.

By:
Nextech
April 11th, 2025
Now that the FDA has officially declared the semaglutide shortage over, patients and prescribers across the country are back to relying on Novo Nordisk to supply the diabetes and weight-loss medication. Regulations about who can prescribe and administer semaglutide, however, continue to vary from state to state.

MedSpa | Regulatory & Compliance | Aesthetics
By:
Nextech
April 10th, 2025
In 2024, intravenous therapy (IV) brought in $2.1 billion in revenue in the U.S. Since the projected revenue is even higher over the next 10 years, opening an IV therapy clinic could be a lucrative endeavor. However, it's only possible to open a clinic – or add the treatment to an existing aesthetic business – if you meet certain licensing requirements.